Mobile application security is a mandatory requirement in the app development process to protect your app from cyber attacks like Malware, DoS and DDoS Attacks, Phishing and Social Engineering Attacks, and Man-in-the-Middle (MitM) attacks. A recent example of such attacks is the one that happened at Meta, formerly known as Facebook where hackers stole the data of 533 million users and posted it on a hacking forum. This stolen data contained Facebook IDs, phone numbers, full names, birthdates, bios, locations, and email addresses.
Protecting your mobile app from such attacks helps build customer trust and loyalty and generate revenue for your business. However, doing it right and efficiently for a large user base can be complicated if you do not have the right information and assistance. You need app security experts to implement effective security solutions and protocols, and prepare your app for any cyber attack that could compromise user data security and privacy.
Cyber Security Threats in Mobile Apps
To prevent and deal with mobile apps security issues, you must learn about the mobile app vulnerabilities that can lead to such cyber security threats.
- Insecure Data Storage
- Insufficient Authentication
- Weak/no Data Encryption
- Infrequent Security Updates
- Server-side Vulnerability
- Excessive Data Exposure
- Insufficient Security Configuration
- Less or No Pen Tests
If not dealt with soon, these vulnerabilities can lead to the below-mentioned cyber attacks in mobile applications.
- Ransomware
- Spyware
- Viruses
- Trojans
- Denial of Service (DoS) Attack
- Man-in-the-middle Attack (MITM)
- Phishing
- Hacking
With the rise in such attacks, the cost of cybercrime worldwide could grow by 15% annually and reach $10.5 trillion by 2025. Even globally renowned platforms like Meta (Facebook) and Twitter are not secure from such attacks. Twitter recently faced a phishing and social engineering attack in which the private credentials of its employees were stolen and used to target over 130 Twitter accounts, some of which were the accounts of celebrities like Kanye West, Elon Musk, and Barack Obama.
Preparing your team/app to deal with and prevent various security threats and vulnerabilities is the best way to avoid many financial and legal risks. The first step in that process would be to implement the legal requirements of app development (such as NDAs, privacy policies, and intellectual property rights).
14 Tips to Improve Mobile App Security
Improving app security is essentially about securing mobile apps from many existing or potential threats that could compromise sensitive user and company data, damage app functionality, and negatively impact the overall user experience.
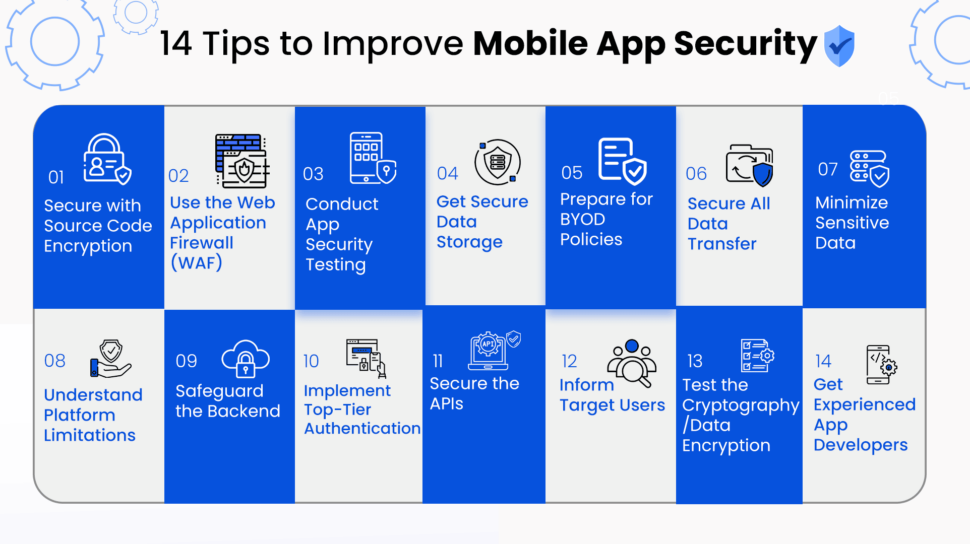
Secure with Source Code Encryption
The source code of an app is a set of instructions that command the application to perform various activities and allow it to process data. Creating a unique source code for an app is a time-consuming and essential stage of mobile app development. However, all of that effort can go in vain if the source code is readable by anyone (usually hackers) once they get access to it. Programming languages like Swift, JavaScript, and Python are easy to read and lead to threats like reverse engineering with malicious code/malware or the creation of copycat products.
For example, when you have a fintech application with advanced functionality and a convenient user experience, a competitor/hacker can access the unencrypted code of your app to reverse engineer the code in order to create a similar product with benefits that your application does not currently provide. While you may be able to legally fight this type of product release for theft and copyright infringement. But a reverse engineering scenario like that could significantly decrease the user base and the business revenue. It is where source code encryption comes in.
Code encryption is the conversion of the source code into another form of language (Monoalphabetic cipher or Alphanumeric Cipher) to secure the original code with a key, ensuring that the original source code can only be accessed by those who have that key. Encrypted source code can seem like gibberish language to those that do not possess the key required to decrypt the code. It protects the original source code and prevents any copycat products and vulnerabilities caused due to the inclusion of malicious code/malware.
Use the Web Application Firewall (WAF)
The benefits of building web applications are apparent to many businesses since the success of apps like Netflix, Spotify, and Amazon. Netflix’s iOS app has 115 million active users every month, while its Android app has about 106 million monthly users. Building such a web app provides the opportunity for revenue growth, but it also creates the need for a web application firewall (WAF) to improve security.
A web application firewall is a reverse proxy that monitors and filters HTTP traffic between the web app and the internet to identify and block malicious HTTP traffic. It protects web applications from SQL injection, file inclusion, cookie poisoning (session hijacking), cross-site request forgery (CSRF), and cross-site scripting (XSS) attacks. WAF is a digital shield that can protect your web application from risky visitors.
Conduct App Security Testing
Frequent app security testing can reveal various weaknesses that could leave an app vulnerable to many cyber attacks and protect its sensitive data. Mobile app security testing can include automated and manual penetration testing (pen testing), static application security testing (SAST), dynamic application security testing (DAST), mobile application security testing (MAST), database security assessment, software composition analysis (SCA), IAST (interactive application security testing), and test coverage. Conducting these tests and more as required will safeguard the mobile application from many existing vulnerabilities and potential threats.
Get Secure Data Storage
The data storage of an application can contain sensitive organizational and user data, theft of which can lead to serious privacy issues and financial risks. Getting cloud storage for application data is the best way to ensure that such data is well-protected. The use of cloud computing in healthcare, fintech, and e-learning sectors is already a popular trend. It is because storing sensitive application data on the cloud has benefits like 24/7 threat monitoring, DDoS attack prevention, tested encryptions, flexible scalability, multi-factor authentications, and data backups.
Cloud computing storage also complies with many data security and privacy laws. Such benefits can protect your data from many security threats and give you a platform to keep storing new data securely. The commonly used platforms for application databases are AWS Storage, MySQL, Amazon DynamoDB, PostgreSQL, and MongoDB.
Prepare for BYOD Policies
This step is only necessary if you are creating employee and company portal apps.
The Bring Your Own Device (BYOD) is a policy that allows employees to use their own laptops and mobile phones for work, which includes accessing official emails, sending and receiving work-related documents, and accessing employee portals. Such a policy can leave user/company data and privacy in the app vulnerable to many threats as IT experts do not regularly check the security of those devices.
You can use mobile device management (MDM) and mobile app management (MAM) solutions to identify, manage, and prevent threats caused by such policies. Make it mandatory for your BYOD employees to use company-provided antivirus and VPNs to secure your company data better. The least popular but effective method is making the security testing of such devices mandatory every month. You will need employee consent to implement such security protocols, which should help you ensure that all your company operations are on tested and secure devices.
Secure All Data Transfer
Hackers can quickly find vulnerabilities in the system to access and steal data during its transfer. For example, hackers may steal sensitive user data by breaking into an insecure chat feature of a social media app. That is why securing all organizational and user data transfers is another step in ensuring improved data security and privacy. Some ways to do that are by data encryption, off-the-record (OTR) messaging, P2P file transfer, PGP and GPG, and Dropbox. Using such methods and tools can help protect official emails and documents from many cyber security threats, whether you are sending or receiving them.
Minimize Sensitive Data
When it comes to online storage, it is not easy or possible to be 100% effective at protecting your data from cybersecurity threats. That is why it is best to analyze the need for confidential/sensitive company data stored in applications, whether it is necessary for the app, and the removal of which data will not affect the app functionality and operations. It should help you remove unnecessary or excessive confidential/sensitive information from the application and keep it secure.
Understand Platform Limitations
Mobile app platforms/operating systems like iOS and Android have limitations when it comes to data security and privacy. Learning about them can help you analyze and determine the additional security measures you have to take to secure your application data. For example, iOS devices are generally more secure than Android devices, with Android devices having significantly more security-related vulnerabilities than iOS devices.
Therefore, your Android app will need better security solutions and more attention than the iOS app. If you are building a cross-platform app, implement security solutions that protect user/organizational data and application servers from various cyber security risks in iOS, Android, macOS, and Windows applications.
Safeguard the Backend
The application backend is the server-side brain of the app that stores, manages, secures, and processes data, which makes it accessible by the front end and ensures its good functionality. That is why securing it from cyber threats is essential to avoid financial and legal risks associated with user data leaks, privacy invasions, and organizational data theft or leaks.
An application backend can face security threats like data injection, leaks, and theft due to poor authentication security, SSL misconfigurations, poor data encryption, and infrequent vulnerability scanning. Ensure that all APIs are tested under reliable mobile app security standards to improve the security of your application backend. You must also get capable app developers to work on the security of your backend if you want to do it right.
Implement Top-Tier Authentication
You must include widely approved and tested authentication systems in your application to protect user data and privacy. Adding biometric authentication like voice recognition, facial, retina scanning, and fingerprint scanning is a great way to start. Many users keep using the same password or pin code for accessing their profiles and data in your app for months. For example, a user may always use the same password to access their profile on a fintech or healthcare application.
Hackers can use this repetitive habit to their advantage and get access to such passwords or pin codes, leaving private medical data or financial data vulnerable to theft and leaks. Adding a combination of biometric authentication, pin codes, and passwords backed up by two-factor (2FA) and multi-factor authentication (MFA) can improve the overall user data and application security.
Secure the APIs
Application program interfaces (APIs) are the intermediaries between two applications that allow them to communicate with each other. For example, when you find and add a destination address in a food delivery or ride-hailing app, you are using a location API implemented in the app during development.
Protecting the APIs you own or use in the application is essential to protect it from data breaches caused by insecure user authentication, fewer resources, insufficient monitoring, and security misconfigurations. You can protect the application APIs with better authentication, tokens, data encryption, API vulnerability scanning, and API gateways.
Inform Target Users
Teaching your users about user data management, security, and privacy protection practices will help you better protect user data, and give your brand a trustworthy image. Users can take several security DIY measures to safeguard their privacy in an application. Check out some of the instructions you can provide to users for better data security and privacy:
- Only download from the App Stores (Google Play and Apple Store).
- Be cautious with device permission in the app.
- Secure the device and app with a strong pin code/password.
- Enable remote wiping.
- Avoid open/public WiFi.
- Do not click on unknown/suspicious links.
- Do not download or remove unnecessary apps.
- Disable Automatic sign-ups and sign-ins.
If users follow precautionary steps like these, it should decrease the excessive use of security solutions for user data and privacy from your side.
Test the Cryptography/Data Encryption
As mentioned above, cryptography/data encryption is essential in mobile application security. It turns your data into a language that is unreadable without a specific key. Cryptography helps transfer confidential/sensitive data securely since even stealing the data does not allow the hackers to read it without the key.
However, testing the integrity of such encryption and decryption is equally necessary to ensure it will do the job. Manually testing the encryption and decryption process should reveal whether it has any vulnerabilities that hackers could manipulate to decrypt and access the data.
Get Experienced App Developers
An experienced mobile app development company will better understand the security measures and updates required for mobile apps in various sectors like e-learning, healthcare, fintech, and on-demand. For example, a food delivery app would not require the same number of security solutions as a fintech application since fintech apps contain a lot of sensitive financial information about users and businesses.
Developers with experience in ensuring reliable mobile security can analyze and determine the security requirements of your application, giving your app the most effective solutions required for data security and privacy.
Final Note
Investing in mobile app security protects your app from viruses, worms, malware, data leaks, hackers, privacy invasion, unauthorized access, data breach, compromised application infrastructure, and organizational data theft/leaks. Such solutions can increase the trust and loyalty of investors, stakeholders, and target users. If you have any further questions about security in your application, talk to mobile app developers to get more insightful answers and guidance/help to make it happen quickly.
Frequently Asked Questions
Mobile application security helps protect sensitive user/organizational data and applications from copycats, data breaches, thefts, and leaks, which could lead to many legal and financial problems.
The secure software development life cycle (secure SDLC) is an approach that includes application security testing at every stage of the development process and after app deployment.
The most effortless way to do that is by hiring professional and experienced developers. They will know what security measures are required for your app, which app security tools to use, and how to improve app security before it is even necessary.






















.png)
.png)
.png)



Leave a Comment